We take a look at the Purdue Model, how it applies to ICS security, and how it can offer security professionals a clear and logical structure for implementing protection
The Purdue Model is a widely used framework for designing and implementing industrial control systems (ICS) security. It was developed in the 1990s by the Center for Information Systems Security Studies and Research (CISR) at Purdue University.
The Purdue model provides a hierarchical structure for ICS architecture that helps to organize the various components of an ICS and enables security professionals to implement appropriate security measures at each level.
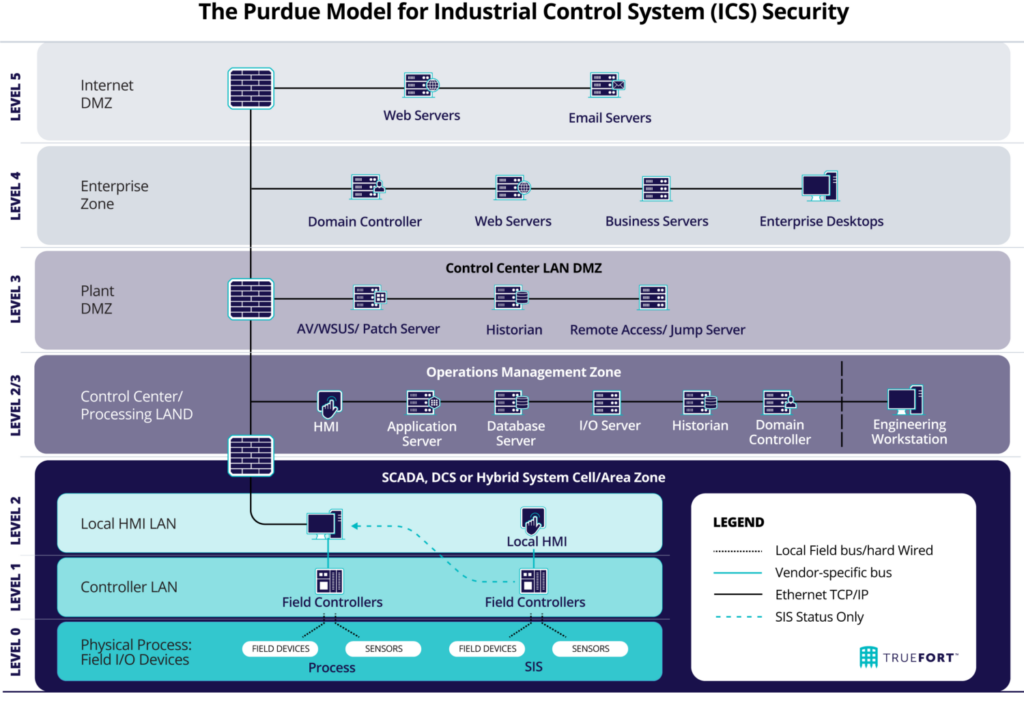
- Level 0 comprises the physical devices that form the foundation of the products, such as motors, pumps, sensors, and valves.
- Level 1 consists of systems that supervise and direct the devices at Level 0, including Programmable Logic Controllers (PLCs), Remote Terminal Units (RTUs), and Intelligent Electronic devices (IEDs).
- Level 2 involves devices that manage the overall processes of the system, such as human-machine interfaces (HMIs) and SCADA software, which enable human operators to monitor and control the system.
- Level 3 facilitates the management of production workflows and includes batch management, manufacturing operations management (MOM), manufacturing execution systems (MES), and data historians. The Industrial Demilitarized Zone (IDMZ) serves as a buffer between the IT and OT networks. The iDMZ helps prevent infections within the IT environment from spreading to OT systems and vice versa.
- Level 4 encompasses systems such as Enterprise Resource Planning (ERP) software, databases, email servers, and other logistics-related systems that manage manufacturing operations and provide communication and data storage.
- Finally, Level 5 is the enterprise network, which is not an ICS environment but collects data from ICS systems for business decisions.
The Purdue Model provides a clear and logical structure for implementing security measures in ICS. For example, firewalls and intrusion detection systems can be implemented at the Supervisory Level to protect SCADA systems, while access controls and authentication mechanisms can be implemented at the Control Level to protect programmable logic controllers (PLCs) and distributed control systems (DCS).
Defining Industrial Control Systems
An industrial control system (ICS) is used to control and automate industrial processes, such as manufacturing, chemical processing, and power generation. An ICS typically consists of a combination of hardware and software components that work together to monitor and control industrial processes with specific functions.
The hardware components of an ICS include sensors, actuators, controllers, and other devices that are used to collect data about the industrial process and control the various components of the process. The software components of an ICS include specialized programs that are used to monitor and control the hardware components. These components sit on a network, in the cloud, or in a combination of the two, often making them vulnerable as a point of entry for attackers.
The Call for Visibility into Device Connections
Visibility into a device’s connectivity is critical for securing industrial control systems. Industrial control systems typically consist of a large number of devices, including sensors, actuators, controllers, and other components. These devices must communicate with each other to perform their functions, and this communication occurs over various communication protocols.
It is important to have visibility into device connections to identify potential security risks, such as unauthorized users and devices connecting to the system, devices communicating over insecure protocols, or devices sending abnormal traffic patterns. By monitoring device connections and knowing what-is-talking-to-what (approved communications), security professionals can quickly detect and respond to potential security incidents outside of baseline behavior and approved operating practices, thus preventing them from causing damage or disruption to the ICS.
In 2017, the NotPetya ransomware attack caused significant damage to the operations of Maersk, a Danish shipping company. The attack started when a single infected device was connected to Maersk’s corporate network, and quickly spread to other devices, including industrial control systems. Over three days, all Maersk tracking operations and associated logistics were offline, causing exponential shipping delays around the globe. It is estimated that there were almost 50,000 infected endpoints and thousands of applications and servers across 600 sites in 130 countries were affected. The attack resulted in significant disruptions to Maersk’s operations, substantial negative PR, and ultimately cost the company hundreds of millions of dollars.
Why Lateral Movement Protection is Important
Lateral movement protection is another critical aspect of securing industrial control systems. Lateral movement refers to the ability of an attacker to move from one device or system to another within IT and consequently move from IT to ICS environment. This can occur when an attacker gains access to a device or system with low-security controls, and then uses that device, system, or user service account to pivot to other devices or systems with higher privileges.
Lateral movement protection involves implementing controls that restrict the ability of an attacker to move laterally from IT to ICS or within an ICS environment. This can include measures such as network segmentation, least access privilege management, and behavioral analysis. By limiting lateral movement, security professionals can prevent attackers from gaining access to critical systems and data, and reduce the potential impact of a security incident.
In 2018, a group of attackers known as Dragonfly 2.0 targeted critical infrastructure organizations in the United States and Europe. The attackers used various techniques to gain access to industrial control systems, including spear-phishing emails and watering hole attacks. Once they gained access to a system, the attackers used lateral movement to move to other systems within the target organization. This enabled them to steal sensitive data and potentially disrupt critical infrastructure operations.
PIPEDREAM has emerged as the latest known industrial control system (ICS)-specific malware, expanding the catalog of such threats. Developed by the CHERNOVITE Activity Group (AG), this advanced malware serves as a modular ICS attack framework that malicious actors can use to scan for new devices, brute force passwords, sever connections, and crash the target device. Depending on the targets and environments, this has the potential to cause untold disruption, weaken security infrastructure, and potentially even genuine real-world harm. Although PIPEDREAM has not been utilized in real-world situations for destructive purposes yet, its potential consequences on ICS environments are causing deep concern for organizations within critical infrastructure sectors. The malware’s adaptable design enables adversaries to tailor their attacks, making PIPEDREAM a flexible and formidable threat, and creating a strong case for comprehensive lateral movement protection.
CISA Cites the Importance of Zero Trust in Securing Industrial Control Systems
Zero trust is a security concept that assumes that all devices, users, and applications are potential threats, and requires that every access attempt be verified before access is granted. Zero trust adoption is particularly important for securing industrial control systems, as these systems are often highly interconnected, and any compromise can have significant consequences.
Zero trust involves implementing controls such as network and microsegmentation, multi-factor authentication, and continuous monitoring. By implementing zero trust, security professionals can ensure that only authorized users and devices are able to access critical systems and data, and that any unauthorized access attempts are quickly detected and prevented.
In 2020, a group of attackers targeted a water treatment plant in Florida and attempted to increase the amount of sodium hydroxide in the water supply to dangerous levels. The attackers gained access to the plant’s control system by exploiting a remote access software vulnerability and then used the system to increase the amount of NaOH. The attack was detected and prevented before any damage was done, but this highlights the critical importance of zero trust in securing industrial control systems.
In response to this attack, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an alert encouraging organizations to implement zero trust principles in their ICS environments. By implementing zero trust, organizations can reduce the risk of attacks like this one by ensuring that only authorized users and devices are able to access critical systems and data.
Effective Purdue Model Implementation
Securing industrial control systems is a critical priority for organizations across all industries. The Purdue Model provides a useful framework for organizing and securing these systems, but it is important to also consider other key aspects of ICS security through Purdue Model adoption, such as visibility into device connections, enforcement through lateral movement protection, and zero trust best practices. Through the implementation of effective security measures at each level of the Purdue Model, and beyond, organizations can significantly reduce the risk of cyber attacks and ensure the continued safe and reliable operation of their industrial control systems.
TrueFort has entered into a strategic partnership with Armis, a leading provider of asset visibility and security solutions. This partnership has resulted in the creation of a single platform that combines asset and business intelligence to address the security challenges posed by the increasing number of connected devices and industrial control systems. The platform is specifically designed to enhance security measures and reduce risks associated with these systems.
If you would like to learn more, please see our strategic partnership announcement.

