Organizations need to go to the same lengths as attackers, but that’s a long way…
When Ellopunk found this in her backpack (℅ Sarah Young) and posted it to Twitter[X] (thank you!), it won the Internet for today, got me thinking, and inspired me to put pen to paper.
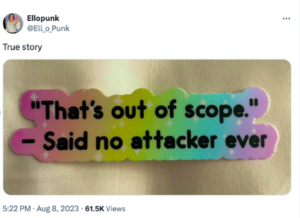
A Cybercriminal Mind Sees Zero Boundaries
Where businesses see barriers, attackers see gateways. Where organizations draw lines, bad actors envision bridges. The phrase “it’s out of scope” seems never to have crossed the mind of an attacker, and they don’t work 9 to 5. When nation-state attackers have eight-figure budgets and time on their side, their determination to breach organizations knows no limits, and their creativity in compromising systems raises the eyebrow of even the most seasoned cybersecurity pros.
Now that I’m thoroughly inspired, let’s delve into a few of the extreme measures these cybercriminals are prepared to take to infiltrate organizations, and briefly explore some of the (many) ways they capitalize on compromised systems. Let’s, as best we can, embark on this journey through the mind of the attacker.
The Never-Ending Pursuit
The world of cybersecurity is, some may say, a ceaseless game of cat and mouse, where defenders build walls and attackers attempt to find ladders. The race is endless, uphill, and the attackers are relentless.
In the words of Charles Xavier, “Mutation is the key to our evolution,” and the adaptability of attacks is worthy of homo superior. Here’s how:
Exploiting the Unexplored
- New Technologies: With the emergence of new technologies, digital infiltrators are constantly finding new vulnerabilities to exploit. Whether it’s the Internet of Things (IoT), exploiting zero-day vulnerabilities, or Artificial Intelligence (AI), each new frontier presents opportunities for attack. Brace for the quantum revolution.
- Supply Chain Attacks: Understanding that they can breach an organization through its vendors, attackers have increasingly targeted supply chains. By compromising one link, they can infiltrate the entire chain, then it’s a hop, skip, and a jump to whatever they want. A call for lateral movement protection, if ever there was one.
- Social Engineering: Even the most robust firewall can’t protect against a deceived human. Through phishing and manipulation, attackers trick the digital unwary into granting them access – with phishing kits and services available on the dark web for pennies and cents.
A Global Reach
- Cross-Border Attacks: National boundaries mean nothing in the virtual world. Attackers from one continent can target organizations on another, making tracking and prosecution incredibly “challenging.” Less extortion and theft, but more digital disruption, the conflict in Ukraine has forever altered cybercrime – and organizations are in the firing line. After achieving its most significant financial confiscation to date, the Justice Department recently announced that it is intensifying U.S. initiatives to battle the global surge in ransomware assaults. The focus will now shift to preemptively disrupting cybercriminal activities before they have the chance to execute.
- Diverse Targets: No one is safe, from large corporations to individual consumers, from governments to non-profits. The scope of targets is as broad as the imagination of the attacker, and, well, let’s just say they must play a lot of D&D.
Money: The Driving Force
Behind the relentless pursuit lies a powerful motivator: hard cash. The financial gains that come from breaching systems are apparently worth the effort. Here’s how attackers turn breaches into profits:
Ransomware Attacks
- Lock and Demand: By encrypting vital data and demanding a ransom for its release, attackers can make serious gains. The City of Atlanta’s ransomware attack in 2018, costing more than 2.6 million USD, is a chilling example.
- Rising Ransoms: As organizations are increasingly willing to pay, the demands continue to grow. Attacks are also becoming more targeted and sophisticated. I suggest a stiff drink before you take a look at some of these recent 2023 cybersecurity statistics.
Data Theft and Sale
- Personal Information: The sale of personal information on the dark web is a thriving business. From credit card details to healthcare records, personal data is a goldmine. Cybercriminals exploit personal data for a myriad of malicious purposes, like committing identity theft, where the stolen information is used to apply for credit or file taxes fraudulently. Additionally, they may sell personal data on the dark web to other criminals who can use it for targeted phishing campaigns, advertising fraud, or other nefarious financial and fraudulent schemes.
- Corporate Espionage: Intellectual property and trade secrets can be worth millions in the hands of competitors, and cybercrime as a service (CaaS) is a very real thing.
Cryptojacking
- Mining Cryptocurrencies: By hijacking systems to mine cryptocurrencies, attackers have found a novel and (arguably) industrious way to make money without even stealing data. It’s like they’ve turned to a digital gold rush, mining virtual riches with stolen shovels and picks. The more systems compromised, the greater the profits, with every computer becoming a potential goldmine and every unguarded network a new frontier to conquer. Cyber-miners say they are “merely embracing the entrepreneurial spirit,” albeit with a morally questionable twist. Their crypto-gold fever pushes them to compromise one system after another, turning unsuspecting devices into exhausted workhorses in their virtual mine. While the rest of us are updating our resumes, they’re updating malware to mine more “gold.” It might be twisted, but you’ve got to (reluctantly) hand it to them for creativity.
Staying Ahead: A Herculean Task
Like cleaning the Augean Stables or putting a duvet cover on a duvet in a moving caravan, the challenge of staying ahead of attackers is monumental. Here’s what organizations must consider:
- Comprehensive Security Posture: Security is not just about technology; it’s about people, processes, and culture. It’s not merely a technical challenge; it encompasses understanding human behavior, fostering a culture of awareness and responsibility, and aligning security practices with the values and needs of individuals and the organization as a whole.
- Continuous Learning and Adaptation: The landscape changes daily. Continuous learning and adaptation are essential. Here’s a few useful cybersecurity resources for those of wearing the white hats.
- Collaboration and Intelligence Sharing: Attackers have active communities. Security teams also need to work together and share information about threats to help everyone stay one step ahead.
- Investment in Advanced Technologies: Machine learning and other technologies can offer predictive and proactive security measures.
- Layers of Defense: A multi-layered security stack means a more robust posture – if they get over the drawbridge, but having the portcullis, the arrow slits, and the boiling oil, is just good practice.
Attackers Don’t Care…
…about scope. The boundaries we see are invisible challenges to the digital criminal. The lengths to which bad actors will go to breach organizations are virtually biblical, and how they capitalize on compromised systems is ever-changing and expanding. Honestly, the things I see daily and their escalation have made me step up my defenses with password managers, my own VPN, and a level of paranoia worthy of Fox Mulder.
But understanding the mindset of an attacker can be the key to staying ahead. Organizations can fight back by realizing that there are no boundaries, recognizing the motivators, and adopting a comprehensive and adaptive security stance. In the eternal race of cybersecurity, the goalposts continually shift.
But with awareness, considered investment, collaboration, and determination, it’s a race that organizations don’t have to lose. Let the phrase “that’s out of scope” be a reminder not of limitations but of possibilities – possibilities for innovation, growth, and robust security.
Prevention is always better than cure.