The Lateral Movement Cyber Security Platform
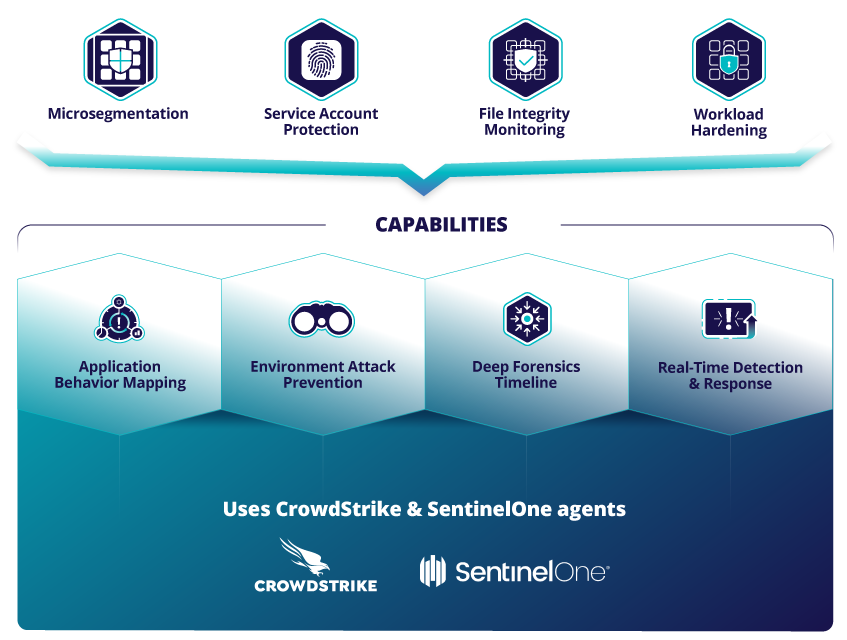
Microsegmentation requires more than firewall rules – only TrueFort prevents attacks from spreading across the most leveraged attack vectors
Gain the visibility needed to take control
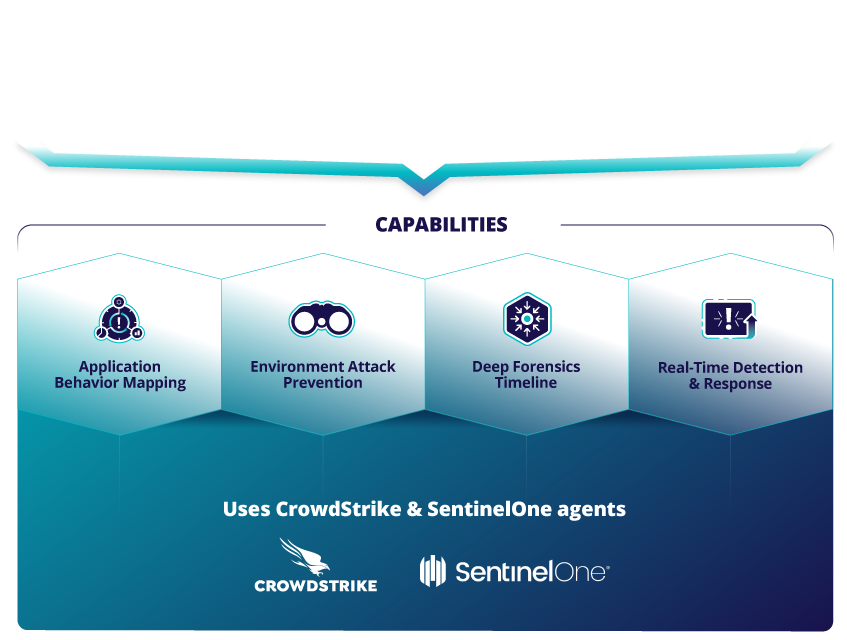
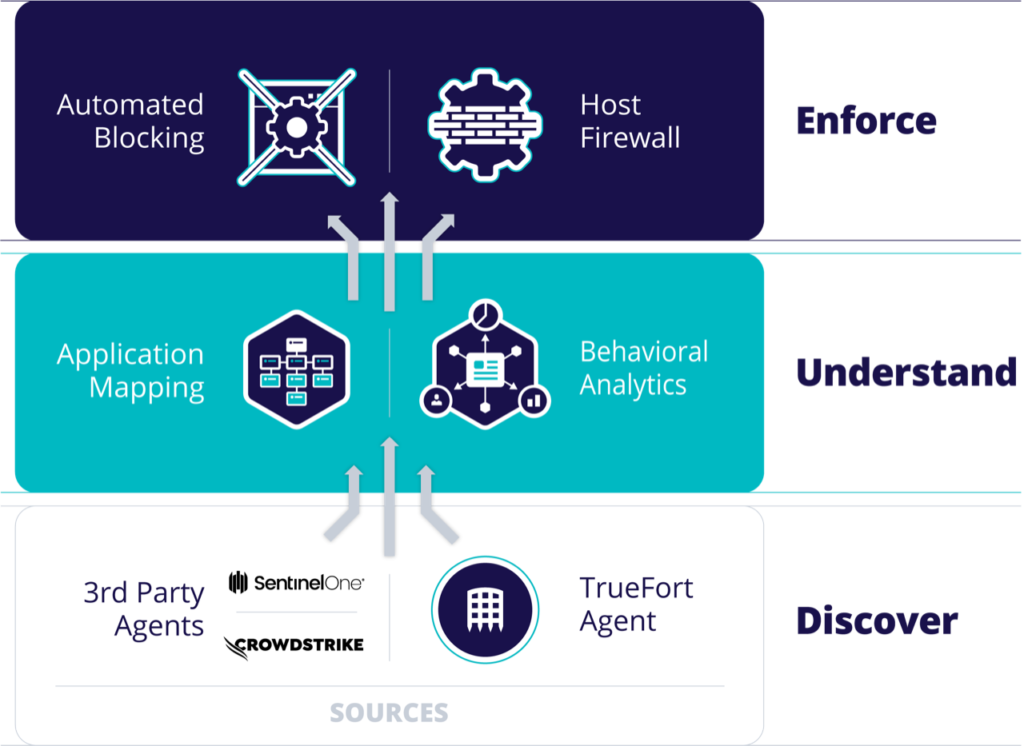
Segmentation projects fail when security teams lack accurate records of how applications operate. Only TrueFort provides a deep mapping of assets operating in the environment and the continuous behavior analysis needed to enforce automated blocking policies. Best-in-class microsegmentation means lateral movement control across network, process, and service account activity.
Learn more about the TrueFort Platform

TrueFort protects some of the world’s largest networks
< 1 Second
Alert and block time on anomalous behavior
> 100,000 servers
Scaled to any size environment
FAQ
Lateral movement is a technique used by cyber attackers to systematically move through an organization’s network as they look for critical data and assets, which become the target of their attacks.
Bad actors want to access sensitive and valuable information while staying undetected. After gaining initial access they will study an organization’s network topology, steal higher profile credentials, and access more systems and sensitive data by moving laterally around throughout the network.
East-west traffic refers to network traffic between devices within a data center, server to server, app to app, or service to service.
As opposed to north-south traffic, which is data packets flowing between systems that are external networks physically outside of the data center, east-west is defined as any communication between two or more components within a specific data center, or even communication between local servers and cloud servers within an organization’s managed boundaries.
Insider threats are potential accidental or malicious risks from users within an organization. This could be from former or current employees, business associates or contractors, and anyone with existing permissions to access an organization’s computer systems and data. These can also be malicious outsiders from the organization, posing as employees or business partners.
Security teams use benchmarking to highlight deviations from usual practices and flag potential insider threats.
If someone other than a designated user has access to account information or user login details, this is known as compromised credentials. This can be passwords, email addresses, or other relevant personal information.
Compromised credentials are often sold on the Dark Web, and bad actors rely on people using the same login information across multiple accounts to gain access. When one account is breached, they conduct credential-stuffing attacks to find other services using the same details.