A closer look at the cloud production environment
Every organization needs an accurate inventory and a clear understanding of a cloud production workload environment to mitigate risk
Most of the emphasis on cloud solutions is usually on ease of use and rapid deployment – which is fair enough because that is what makes them such an attractive option for organizations. As the cloud environment continues to explode across the enterprise, however, managing and maintaining observability of workloads and applications has become a pain in the side for our security teams. Let’s take a deeper look at the risks around an unmanaged cloud environment, the challenge of keeping an accurate inventory, and some practical approaches to solving the problem.
Having spent many years working with teams in a broad cross-section of industries, from aviation to IT support and from banking to state agencies, it’s clear that maintaining production environment observability for cloud-hosted workloads and applications is easier said than done. Keeping track of a metric tonne of dependencies, behaviors, and other attributes required for cyber protection and somehow wrangling this into an actionable view of the data is a water cooler grumble I’ve heard often.
Strategies for observability
Working with the team here at TrueFort, I’ve come to understand that solid strategies do exist to shine a light behind the curtain of the production cloud workload environment. Indeed, it’s like catching Oz the Great and Terrible in the headlights of an SUV, and can all be done without further burden on the application security specialists, operations staff, or application development team.
Observing dependencies – One of the main differences between those old applications hosted in traditional data centers and the bright and shiny modern applications running in virtualized cloud environments is an obvious growing need to understand and managing the resulting network of communications and dependencies that comes with the advantages of cloud functionality. Workload and application communications are a major byproduct of a microservice architecture built on containers and orchestration.
Gaining intelligence from behaviors – Getting real intelligence about a production application can only be achieved through active observation of live behavior. Sure, status reviews and testing provide helpful context, but only through the observation of communications and dependencies can we get real-world intelligence and practical insight. With knowledge comes power, as they say, and that intelligence can be used to drive real action – dimming down those time-consuming false positives.
Covering hybrid architectures – The need to observe application behavior is especially important for hybrid architectures supported by multiple public cloud services. Whenever a hybrid approach is taken, security teams must rely on different reporting tools that can be inconsistent and incompatible. Therefore, maintaining a common level of visibility across a hybrid base is essential to build an accurate view of production-level posture.
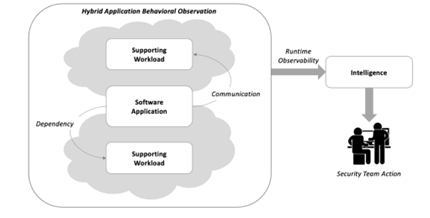
Figure 1. Advantages of Production Application Observability
Lifecycle visibility
Establishing early visibility during DevOps is essential to the entire lifecycle, including production deployment. A common mistake in cybersecurity (across all types of controls) involves waiting until the production deployment has been completed to put security controls in place. It’s far more efficient and cost-effective to begin the security integration process as early as possible, during development – and this is undoubtedly true for modern applications.
Observation is invaluable. There’s tremendous value in shining that light on application behavior across hybrid infrastructure during all aspects of the lifecycle – including the production-hosted runtime instance. Only through such dynamic, ongoing observational infrastructure can security teams make good security decisions about a running software application.





