The foundation of successful cloud adoption is the definition and management of a strong micro-segmentation strategy. The ability to minimize trust relationships and enforce predefined application and workload behavior provide a solid underpinning of a secure cloud environment.
Micro-segmentation is one of the critical pieces of functionality by which enterprises can build a secure cloud deployment. Microsegmentation lays the groundwork for the enforcement of controls at a granular level, minimizes unrestricted enterprise movement, deals with abuse of cloud-based permissions, and provides a baseline for how applications are expected to work.
We (TrueFort) approach microsegmentation from the perspective of lateral movement after compromise. The goal is to manage network connections and service accounts to protect workloads, reduce attack surfaces, and secure the local infrastructure. We meet these objectives via application intelligence and agent deployment, which we look into further below.
Application intelligence
The first requirement for microsegmentation deployment involves identifying dependencies, interactions, and sharing between the microsegment and its surrounding environment and entities. This is easier said than done because it requires insight into both the run-time and static characteristics of the microsegment and its associated workloads and applications.
The need to highlight dependencies follows the shift from the deployment of monolithic applications in corporate data centers to the microservice-based deployment of containers in cloud and SaaS environments. One can visualize the resulting interactions between application components as a mesh, supporting data transfer, sharing, and communication.
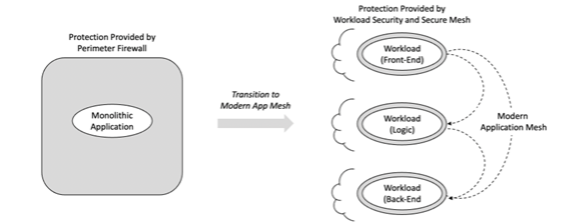
Figure 1. From Monolithic Apps to Mesh-Based Deployment
Our platform supports this demand for visibility by deriving intelligence about the operation and use of an application. This involves pulling telemetry from the interactions and communication that emerge in a modern hybrid deployment. Everyday use cases include business logic interacting with front and back-end systems for data.
The result is support from TrueFort for this application intelligence, and as suggested above, this provides a foundational base for microsegmentation. It replaces the data output shared by a next-generation firewall (NGFW) at the corporate perimeter with a platform-based collection of telemetry data across the application mesh.
Agent deployment
The second requirement for microsegmentation involves ensuring a secure interaction between the hosted workloads and their surrounding environment. The good news is that cybersecurity has become sufficiently mature to offer many excellent commercial options to implement the desired controls for this type of arrangement.
To that end, we’ve partnered with commercial endpoint security provider CrowdStrike to integrate directly with the popular Falcon platform. This enables the use of an existing Falcon deployment to achieve the cybersecurity goals for zero trust discussed earlier. Specific features enabled via the TrueFort and CrowdStrike partnership include
- Agent Reuse – For existing Falcon customers, no additional agent is required to engage the application intelligence or microsegment enforcement provided by TrueFort.
- Unified Visibility – Enterprise teams with an existing Falcon deployment can direct TrueFort telemetry to this platform to enhance and improve the quality of the visibility.
- Detection and Response – The application intelligence offered by TrueFort can more directly connect with immediate detection and response processes.
With most modern cybersecurity tools, the key issue has become their ability to interact and integrate with other existing platforms and tools – simply because cybersecurity at the enterprise level now includes existing deployed controls. Our partnership with CrowdStrike is indicative of this positive trend.
Recommended strategy
The practical implications for enterprise teams desiring a proper microsegmentation strategy is that the following steps should be included in all management planning related to this common initiative:
- Step 1: Ensure visibility – Ensure a plan is in place to develop application intelligence and insight into the interactions that inevitably exist between workloads in a modern mesh arrangement across multi-cloud.
- Step 2: Review integration options – Make sure to review and take full advantage of options to integrate planned commercial tools via their application programming interface (API) or through -pre-planned integrations such as with TrueFort and CrowdStrike.
- Step 3: Work with capable vendors – Always select and work with capable vendors who can guide day-to-day tactical and longer-term strategic decisions toward options that reduce cost, reduce risk, and maximize value.
Following these management steps in all planning and execution activity toward a microsegmentation-based deployment will help to reduce the risk for both operational workloads and also for overall project management.





